Advancements in technology also mean greater cyber-attacks to the diverse information technology infrastructure the world is thriving on now. Since ways to breach this infrastructure is unique, cybersecurity domains need to be even more creative with their solutions.
Cybersecurity solutions need to have a targeted solution for every step, along with an overall focus on security.
Having a general sense of cybersecurity framework is no longer enough.
An intricate web of security measures, layered on top of one another are what consolidate cybersecurity domains.
📌 Table of Contents
What are the domains of cybersecurity?
Cybersecurity domains are the intricate web of multiple cybersecurity measures working together to protect a system.
There are many domains covered in cybersecurity mind maps.
In order to have a complete cybersecurity mind map, one needs to have the information of as many information security and cyber security domains as possible.
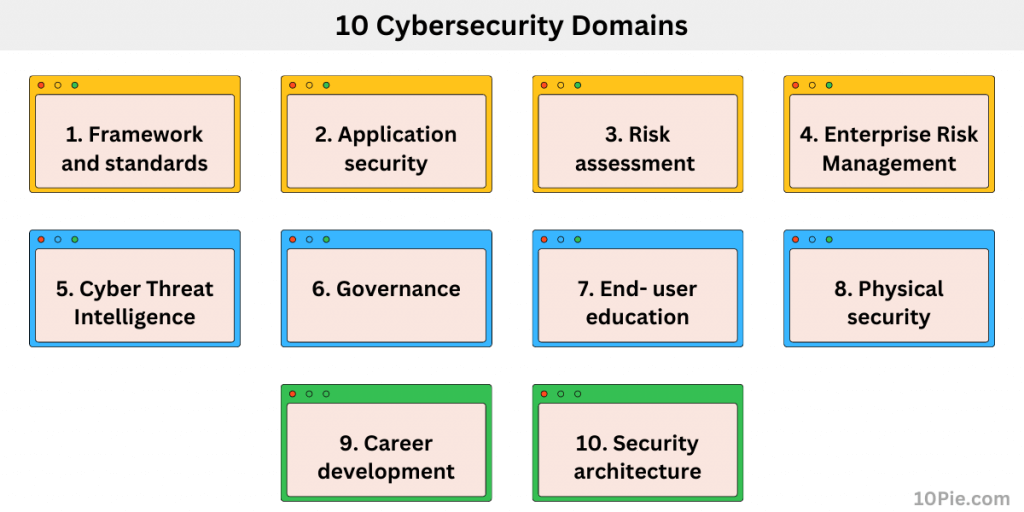
1. Framework and standards
The overall cybersecurity framework in any organization is the framework domain it follows. It is a combination of many domains working simultaneously.
- Overall structure of cybersecurity makes a framework: A mix of many cybersecurity frameworks and have sub- sections of cybersecurity measures in them.
- Cover multiple levels of tasks at a glance: Allows you to work on multiple plains of cyber- attacks, all at once
- Have greater control over other domains: Determine risk tolerance and set controls
- Customize each cybersecurity system: Many cyber frameworks and standards can be applied together onto one system
2. Application security
Many efforts have to be put in to ensure the safety of a software once it is out in the market as well. Application Security is the only way to ensure the security of all the stakeholders involved in the software process.
- Provides added protection to software: Allows you to install many layers of security within a software and to any information related to it
- Have greater control over software information: Limit unwanted changes to the software information
- Add better security to applications: Allows you to implement secure codes, threat modeling, etc.
- Secure existing applications: Ensures security of existing software and applications
3. Risk assessment
Analyzing an organization for any potential risks that may come up in the future, breaching cybersecurity walls. However, it also works to neutralize current risks as well. It determines what kind of threat it possesses, if any.
- Focus on targeted cyber threats: Identify hazards and risk elements in cyber security measures.
- Analyzing risk is important: Analyze how the risks are to be dealt with, assess the risk accordingly.
- Prevent future cyberattacks: Administer solutions to prevent further damage and similar attacks in the future.
- Analyze future cybersecurity framework: Accessing the likelihood of impact from future cybersecurity threats.
4. Enterprise Risk Management (ERM)
Risk management within a company’s internal functioning is a part of ERM. Awareness within employees is a much more effective method at neutralizing risks than just having a dedicated team towards it.
- Analyze cyber risks beforehand: Risk management with an organization’s cybersecurity framework
- Efficient use of cyber resources: Risk acceptance that controls resource allotment in risk management
- Prepare the organization for higher risk appetite: Crisis management and allows in- depth analysis of risk appetite of the organization
- Analyze business growth: Monitoring business regularity, reputation and brand value constantly
5. Cyber Threat Intelligence (CTI)
It is also known as Cyber Threat Intelligence that allows an organization to collect information from a number of resources to analyze and isolate any potential cybersecurity threats.
The threats that are analyzed are acted upon quickly in order to minimize the potential cyber risks it carries.
- Quantitative data collection: Collecting information on past and potential cyber threats.
- Assist other cybersecurity domains function better: Always used along with other cybersecurity domains.
- Holistic protection to database: Can protect against internal and external cybersecurity threats.
- Bring out the efficiency in functioning: Can assist other cybersecurity domains function better.
6. Governance
The strategy of any organization to deal with potential and real cyber security attacks. Allows organizations to develop better cybersecurity measures.
- Governs different cybersecurity processes: Process of decision making and implementation of cybersecurity measures
- Helps reduce cyber attacks: Risk analysis is aided with Governance and decisions can be taken on time
- More cost efficient: Allows organizations to be more cost efficient by creating better rules and regulations in place
- Better policy formulations: Aids in creating a better company policy on various aspects of internal and external security
7. End- user education
Allows employees to be better informed on data hacks and data losses. This will prevent unnecessary attacks in the first place or they will be able to identify risks in the first place themselves.
- Make everything secured: Gather more education on information security domains, which only deals with protecting information and information systems.
- Everything is encrypted: Work through confidentiality, integrity and availability as a part of end- user education.
- Include daily exercises to be more functional: Engage in cybersecurity tabletop exercises, training and information security education as part of end-user education.
- More protected data: Better protection against data hacks and data losses with the right tools.
8. Physical security
The cybersecurity of any organization can run smoothly when the physical assets of the company are safeguarded. The cybersecurity systems need a secure physical location to operate as well.
- Address the threat more directly: Growing complexity of physical cybersecurity can be addressed through physical security threat analysis
- No more threat from AI: AI and internet of things challenge physical cybersecurity as an ever growing threat
- Physical damage is possible: Damage to physical assets can hamper people and property of the organization
- Helpful for cyber teams: Cyber teams need to protect physical assets of the organization as well.
9. Career development
If cybersecurity and cyber attacks have become sophisticated, so has the demand for properly qualified cybersecurity personnel. It is important to have the right people on your team to ensure the best defense and services for your organization.
- Excel through various trainings: Get the right certifications, training and self- study the different domains, if you come across something new and different
- Be updated on the latest certifications: Getting the right certifications and being constantly updated through them like the CISSP (Certified Information Systems Security Professional)
- Be in the know of the best in your industry: Be on top of all new developments in cyber security
- Learn the right hacking skills: Ethical Hacking is a great new cybersecurity certification that can actually help organizations.
10. Security architecture
A cost effective and efficient security architecture that would allow you to address the existing and potential threats that the organization may be under.
There are many categories that need to be taken care of in security architecture like legal aids, financial aid, risk management and many more.
- Provide the right environment to cybersecurity team: Giving the cybersecurity team the right environment to ensure that the potential risks can be taken care of.
- Logical implementation: Risk assessment and risk analysis in a logical manner that is deliverable and sustainable
- Security architecture: Proper documentation of the creation of this security architecture and the steps that this domain takes on.
- More efficiency in the process: Security architecture specifies the optimum conditions to take of all domains.
📌 Related resources
What are the best cybersecurity domains?
It is difficult to have just one cybersecurity domain that your organization is focusing on. They all are a part of a larger system that combines to be termed as a cybersecurity system.
They all combine to create a well- functioning security system, which is the ultimate goal for any organization.
Different organizations have different needs. This is what may lead to a difference in the kind of cybersecurity domains that they may need.
However, no cybersecurity domain can exist in isolation. They most certainly need an amalgamation and combination of different cybersecurity domains in order to have the best protection for any organization.
📌 Related read:
What are the risks and threats of the user domain?
Here are some of the common risks and threats of the user domain in cybersecurity:
- Hacking, phishing, impersonation, and data leaks are potential risks and threats to the user domain.
- These attacks can be deliberate or accidental in nature.
- The purpose of cybersecurity is to prevent accidental leaks and isolate threats in time.
- Accidental threats occur when employees are not aware of the possibilities of their actions, such as sharing passwords or sensitive information on social media.
- Specializing in one domain of cybersecurity can create a niche in your career.
- Investigating accidents and identifying the root cause is crucial in preventing future threats.
- User domain threats can originate from within the organization.
- Having the right experts in cybersecurity is key to dealing with threats effectively.
- The more devices an organization uses, the more vulnerable they are to threats.
- Attackers are becoming more creative, but so are cybersecurity measures.
- Implementing the right cybersecurity measures is essential in protecting against threats.
📌 Learn more about Beginner’s guide to cyber security pros and cons
Comparison between cybersecurity domains
| Domains | Purpose | Key Features |
| Framework and Standards | Determine risk tolerance and set controls. | Allows for multi-dimensional protection. |
| Application Security | Ensure the security of existing software and applications. | Implement secure codes, threat modeling, and secure information. |
| Risk Assessment | Identify and neutralize potential and current risks. | Assess impact and administer solutions. |
| Enterprise Risk Management (ERM) | Internal risk management within a company. | Resource allotment, crisis management, and risk analysis. |
| Threat Intelligence (CTI) | Collect information to analyze and isolate potential threats. | Protects against internal and external threats. |
| Governance | Develop better cybersecurity measures. | Cost-efficient, better company policy, and decision making. |
| End-User Education | Educate employees on data protection. | Confidentiality, integrity, availability, and tabletop exercises. |
| Physical Security | Safeguard physical assets of the company. | Address growing complexity and protect people and property. |
| Career Development | Qualify cybersecurity personnel. | Obtain certifications, stay updated, and ethical hacking. |
| Security Architecture | Deliverable and sustainable risk assessment and analysis. | Logical and sustainable documentation. |
Final words
Cybersecurity is vast and complex. There are many domains that come under the complexity of cybersecurity.
The domains mentioned above are the standard domains applied everywhere.
However, the growing demands and problems of these threats have led to further advancements in understanding the potential ways to neutralize these threats.
FAQs on cybersecurity domains
1. What is a domain in cybersecurity?
In cybersecurity, a domain refers to a network or a group of computers and devices that share a common security policy and administrative authority.
2. Which domain is best in cybersecurity?
The best domain in cybersecurity depends on an individual’s interests, skills, and career goals. Some popular domains include network security, cloud security, and cybersecurity management.
3. How many security domains are there?
There is no fixed number of security domains, as the cybersecurity field is constantly evolving and expanding.
However, some commonly recognized domains include network security, application security, and cloud security.

Smriti Mathur holds expertise in the tech field. She has practiced on a vast amount of data and is equipped with state-of-the-art algorithms, capable of understanding and analyzing complex technological concepts and trends.
Her proficiency in machine learning and data analysis allows her to provide valuable insights and perspectives on various aspects of the tech industry, including artificial intelligence, cybersecurity, cloud computing, and software development.
With a deep passion for technology and innovation, she strives to stay up-to-date with the latest developments and trends in the field, constantly learning and expanding her knowledge base.
Whether you’re a tech enthusiast, a startup founder, or an industry expert, Smriti is writing valuable content to share her expertise and help you navigate the ever-evolving world of technology.