Yes, cybersecurity requires various knowledge and concepts to protect systems and information from cyber threats.
In this guide, we will highlight why mathematics concepts are important to become a cyber security analyst and how math is used in this field.
Also, you’ll learn various mathematics concepts and areas that you should focus on to become a successful cybersecurity engineer in 2023.
📌 Table of Contents
What Is Cybersecurity?
Cybersecurity is the use of several technologies, practices, and processes to protect computer systems from malicious software, networks, and data breaches. The end goal of cybersecurity is to provide system administrators with security, confidentiality, integrity, and proper availability of information from other systems connected through the internet safely.
How Is Maths Used In Cybersecurity?
Although you can start your cybersecurity career without deep knowledge of maths, you should know that maths is a core part of cybersecurity.
Different algorithms and mathematical models are essential in securing communication and providing a foundation for cryptography.

1. Cryptography In Cybersecurity
Cryptography is a technique of securing data when communicating over the internet, and it plays a significant role in the development and innovation of cybersecurity.
There is a long list of concepts of the math behind cryptography, which include discrete algebra, integer factorization, number theory, combinatorics, and elliptic curves. The most widely used algorithms are RSA and DH. Discrete logarithm makes these algorithms.
Deep knowledge of mathematics is fundamental to implementing cryptography properly because more advanced lattice-based cryptography like NTRU and FHE are gaining ground.
Thus, you need to know different mathematical concepts to encrypt and decrypt data. Therefore, knowledge of mathematics for cyber security is beneficial.
2. Simulation and Testing of Cybersecurity Systems
Mathematics plays a crucial role in the simulation and testing of cybersecurity systems.
Simulation modeling deals with the representation of the systems happening in the real world using a virtual environment. When engaging in simulation modeling, you will require a good understanding of probability and statistics.
Before providing the security features to the masses, you must test the performance and security. The testing and validation process requires using various mathematical metrics and analysis of different statistics.
For example, some mathematical concepts used in testing and validation include false positive and false negative rates, receiver operating characteristic curves, and entropy measures.
3. Data Analysis
In cybersecurity, people have to deal with large datasets. Thus, to deal with such complicated data pools, you must implement different tools and techniques to understand everything effectively, making data analysis and the knowledge of data implementation and statistics vital.
Cybersecurity officials use statistical analysis to find patterns and abnormalities in concrete data pools. It can also help find unauthorized activities and potential virus threats.
There is also a requirement for data analysis in machine learning, and the better the machine learning model, the better the detection of patterns and classification of various datasets.
You need good data visualization skills, which will help you quickly find patterns in histograms and heat maps containing complex data.
4. Network Design And Optimization
You can use mathematics in network designing and optimization in cybersecurity in many ways. For example, mathematical concepts like graph theory and linear algebra are essential for network topology design, which involves mapping the arrangement of nodes and links in a network.
Network topology design is essential for security and maintaining the efficiency of the network.
Probability theory, decision theory, and Bayesian theory is involved in assessing risks in a network. In addition, using linear and integer programming and game theory is fundamental to implementing effective resource allocation for efficiently using bandwidth and computing power.
5. Cryptanalysis
Cryptanalysis is a way of getting hold of the meaning of the encrypted information without access to the secret key. Wherever you see analysis, you require mathematics there. Different concepts like number theory, algebra, probability, statistics, and other analytical methods are required to analyze and decipher cryptographic entities.
There is a requirement to implement various mathematical models and simulations to study the behavior of cryptographic models. It can also help discover the cybersecurity system’s potential weaknesses.
Thus, there is a reasonable requirement for mathematics in the field of cryptanalysis in cybersecurity.
Applications of math in cybersecurity
| Application of Math in Cybersecurity | Description |
|---|---|
| Cryptography | Cryptography in cybersecurity is a method to protect your information by making it unreadable to unauthorized access. Mathematical concepts such as prime numbers, modular arithmetic, and discrete logarithms are generally used in cryptographic algorithms to keep data safe and secure. |
| Network Security | Network security is the process of protecting computer networks from cyber attacks, unauthorized access, and other potential cyber threats. In network security, math concepts like probability theory and graph theory are used to detect and prevent cyber-attacks. |
| Malware Analysis | Malware analysis is the study of malicious software, including viruses, Trojans, and worms. Mathematical modeling is employed in analyzing the behavior of malware and identifying patterns that can be used to detect and eliminate the malware. |
| Digital Forensics | Digital forensics experts use mathematical concepts (such as linear algebra, probability, etc.) to analyze the digital evidence they are presented with. This involves identifying patterns in the data or using algorithms to detect anomalies. They also use specialized tools to examine data more closely, such as virtual machines and disk imaging software. |
| Security Analytics | Security analytics is the practice of identifying and responding to potential security threats using data analysis and machine learning techniques. Here, math concepts such as statistics, data mining, and machine learning are used to detect anomalies and patterns that could indicate a security threat. |
| Risk Assessment | Risk assessment is the process of identifying potential threats and vulnerabilities, and assessing their potential impact on the organization. In this case, probability theory, statistics, the basics of number theory, and linear algebra are useful. |
What Math Is Needed For Cybersecurity?
You must implement various mathematical concepts and techniques to shine in your cybersecurity career. These concepts can range from number theory and algebra to probability and statistics.
Let’s learn the mathematical concepts you should know to do good in cybersecurity.
1. Number Theory
Number theory concepts play an essential role in the field of cybersecurity. You need these mathematical concepts to create and analyze cryptographic systems like the RSA algorithm. Under number theory, various subconcepts are essential, like studying prime numbers, modular arithmetic, and integer properties.
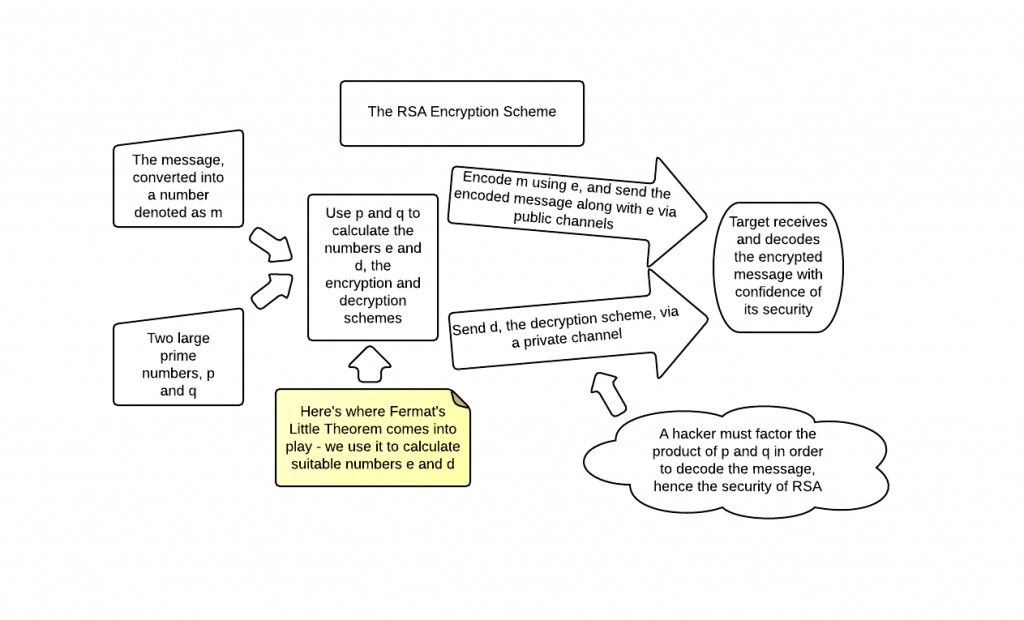
Number theory plays a vital role in the implementation of secure encryption algorithms, which help in the protection of information from unauthorized sources, and helps maintain the integrity of the data.
2. Algebra
Algebra also plays a critical role in cybersecurity. Algebraic techniques are must-know concepts to design and analyze complex cryptographic and network systems. An essential concept of algebra used in cybersecurity includes group theory, a branch of abstract algebra used in the analysis and design of cryptographic systems. Cybersecurity officials also use elliptic curve cryptography, an algebraic technique, to design new encryption algorithms.
Linear algebra helps in the coding and decoding of algorithms using the concepts of linear transformation. Furthermore, by helping in the efficient detection and correction of errors, linear algebra also helps ensure digital communications’ accuracy and reliability.
3. Probability and statistics
Probability and statistics are the core concepts required to analyze and model the complex system’s behavior so that the systems can make correct decisions according to the data provided. In addition, the officials require these concepts to effectively analyze the cryptographic systems and performance of the intrusion detection systems.
Probability and statistics can help analyze how dreadful the security threat can be and the risks associated with any data breach or cyber-attacks. It can predict the scale of damage that a data breach or malware can do.
Statistics play an essential role in analyzing the behavior of malware and finding the patterns in security threats.
4. Information theory
Information theory in mathematics studies information like data representation, storage, and transmission. It helps in designing and analyzing secure communication systems and understanding why a system behaves in a particular manner. Thus, information theory is essential when implementing machine learning in cybersecurity systems and models.
Information theory also helps in the efficient analysis of error-correcting codes. It helps to know how reliable digital communications are through the system. It is a mathematical concept that will help you know the uncertainty and randomness in a system, better known as the entropy of a system.
Math in information technology is a core subject. Thus, information theory is essential for analyzing and understanding complicated systems and many other cybersecurity functions.
5. Graph Theory
Graph theory is one of the most vital concepts of mathematics that has excellent utility in cybersecurity. Using graph theory, officials can efficiently understand the interactions between different elements in a cryptographic system. They can also use this mathematical concept to model and check if the network systems behave perfectly.
Using graph theory, people can analyze the internet’s structure and pinpoint the vulnerable areas which may fall victim to cyberattacks. Thus, graph theory is one of the most critical concepts to help analyze systems and check if a network is healthy.
6. Combinatorics
The branch of mathematics that deals with the counting, arranging, and analysis of finite object collections. It has many applications in cybersecurity, among which two of the core used cases are cryptography and password cracking.
Combinatorics helps design and analyze cryptographic systems like public-key cryptography, symmetric-key cryptography, and message authentication codes. Other than combinatorics, cryptographic systems also require permutations, combinations, and number theory concepts.
Using permutations and combinations, cybersecurity officials can implement combinatorics to crack passwords. Combinatorics also has its use in designing many network security protocols like firewalls, intrusion detection systems, and VPNs.
7. Geometry
Geometrical concepts are also essential in the field of cybersecurity. Primarily, it has use cases in cryptography, visual cryptography, network security, and image processing. For example, the use of elliptic curves and lattices to design public-key cryptography algorithms like ECC or Elliptic Curve Cryptography and lattice-based cryptography is prevalent today. These algorithms help users securely transfer encrypted messages over the internet.
These algorithms also help efficiently encrypt images and visual data using cryptographic keys. Geometrical concepts also help in designing secure communication networks like VPNs. Thus, geometry concepts are a significant part of your childhood syllabus and play a considerable role in cybersecurity.
Further resources of cybersecurity:
- Advantages and disadvantages of cybersecurity
- Impact of modern technologies in the cybersecurity field
- Top cybersecurity documentaries to watch
- What career to choose between cybersecurity vs computer science
What Is The Role Of Maths In Cybersecurity?
By now, you should have known that mathematics is vital to consider when aspiring to take up cybersecurity as a career option. Furthermore, you should be aware that math and cyber security go hand in hand. However, cybersecurity math requirements aren’t too much. Thus, let’s quickly summarize the role of maths in the field of cybersecurity.
- Mathematical concepts are the foundation for designing and implementing many algorithms and protocols to fight malware and cyber threats.
- Several mathematical concepts, like number theory, encryption, computational complexity, etc., help make communication systems, authentication methods, and secure key exchange protocols safe and efficient.
- Cryptography, hashing, and digital signatures require confidentiality, and mathematics helps in making algorithms that help keep the data hidden from cyber criminals.
- Mathematical concepts are essential for analyzing systems and predicting the magnitude of a potential data breach and malware attack.
What Kind Of Math Do You Need For Cybersecurity?
By now, you should also know the different domains of mathematics and concepts you should be aware of in case you aspire to become a cybersecurity official. But first, let’s recap what kinds of mathematical concepts you should be aware of.
- Number theory is an essential mathematical concept used in the field of cryptography in the creation of public keys and secure communication systems.
- Linear algebra helps in the study of encryption algorithms and the designing of secure protocols.
- Probability and statistics combined help in the assessment of risk and threat elimination and assessment.
- Graph theory helps in network security assessment and in designing secure communication systems.
- Game theory typically helps build machine learning models and uses it to model and analyze decision-making in the systems.
There are many other concepts that one has to be aware of to make a promising career out of cybersecurity. As the field develops, more and more mathematical concepts will add up. Thus, maths will become a core element in learning cybersecurity.
How Is Math Used In Computer Networking?
Mathematics plays a crucial role in computer networking in the field of cybersecurity. Several network security protocols, like IPSec and the SSL, use mathematical models and algorithms for encryption and decryption when transferring data over the internet. In addition, public-key cryptography is used to keep the data confidential and genuine, and any form of cryptography requires mathematics.
If you’re looking to start your career in cybersecurity, check out our cybersecurity courses for Mumbai based on metrics like placement assistance, pricing, rating, and syllabus.
Does Computer Networking Involve Math?
Yes, computer networking does require mathematics. There are many places where you can use mathematics in computer networking. Some of these include:
- Its primary use is placing network nodes and driving the data between them. It is known as network design and is a vital part of computer networking.
- Mathematics also helps in data transmission, which helps correct errors and compresses data to ensure smooth and authentic data transmission through the systems.
- In cybersecurity, maths help in cryptography, hashing, and designing digital signatures for the safe flow of data and protection from cyber criminals.
- If you wish to know how your system is performing, you must implement algorithms that require mathematics. Thus, to check the system’s outcome, you have to know probability and statistics, which are part of mathematics.
FAQs on cyber security math skills
1. Does cybersecurity involve a lot of math?
Yes, cybersecurity does require you to learn a good chunk of higher mathematics because it has applications everywhere in the field.
However, when beginning with cybersecurity, you won’t need it, but with time you have to know many mathematical concepts.
Thus, the question of ‘how much math in cyber security’ gets solved.
2. What are the specific areas of cybersecurity that require math skills?
You will require math skills in cryptography, network security, machine learning, and developing artificial intelligence (AI) models.
3. What are the key mathematical concepts used in cryptography?
The fundamental mathematical concepts used in cybersecurity include number theory, different forms of algebra like linear algebra and boolean algebra, graph theory, probability, statistics, etc.
4. Is cyber security a hard subject?
No, cybersecurity isn’t a challenging subject. However, to get a deep understanding of the field, you should be enthusiastic and always passionate about learning and implementing new things. Read this guide on why cybersecurity is not that hard to learn for beginners.
10Pie Editorial Team is a team of certified technical content writers and editors with experience in the technology field combined with expert insights. Learn more about our editorial process to ensure the quality and accuracy of the content published on our website.

